# Pomerium using Docker
In the following quick-start, we'll create a minimal but complete environment for running Pomerium with containers.
# Prerequisites
- A configured identity provider
- Docker and docker-compose
- TLS certificates
# Configure
# Configuration file
Create a configuration file (e.g config.yaml) for defining Pomerium's configuration settings, routes, and access-policies. Consider the following example:
# See detailed configuration settings : https://www.pomerium.io/docs/reference/reference/
# this is the domain the identity provider will callback after a user authenticates
authenticate_service_url: https://authenticate.localhost.pomerium.io
# certificate settings: https://www.pomerium.io/docs/reference/certificates.html
autocert: true
# REMOVE FOR PRODUCTION
autocert_use_staging: true
# identity provider settings : https://www.pomerium.io/docs/identity-providers.html
idp_provider: google
idp_client_id: REPLACE_ME
idp_client_secret: REPLACE_ME
# Generate 256 bit random keys e.g. `head -c32 /dev/urandom | base64`
cookie_secret: WwMtDXWaRDMBQCylle8OJ+w4kLIDIGd8W3cB4/zFFtg=
# https://www.pomerium.io/configuration/#policy
policy:
- from: https://httpbin.localhost.pomerium.io
to: https://httpbin.org
allowed_users:
- bdd@pomerium.io
Ensure the docker-compose.yml contains the correct path to your config.yaml.
# Autocert Docker-compose
Ensure you have set up the requisite DNS and port forwarding in TLS certificates
Download the following docker-compose.yml file and modify it to:
- generate new secrets
- mount your TLS certificates
- mount your
config.yamlconfiguration file - Set
autocert_use_stagingtofalseonce you have finished testing
version: "3"
services:
pomerium:
image: pomerium/pomerium:latest
environment:
# Generate new secret keys. e.g. `head -c32 /dev/urandom | base64`
- COOKIE_SECRET=V2JBZk0zWGtsL29UcFUvWjVDWWQ2UHExNXJ0b2VhcDI=
volumes:
# Use a volume to store ACME certificates
- pomerium:/data:rw
ports:
- 443:443
# https://httpbin.corp.beyondperimeter.com --> Pomerium --> http://httpbin
httpbin:
image: kennethreitz/httpbin:latest
expose:
- 80
Please note that you should use a persistent volume to store certificate data, or you may exhaust your domain quota on Let's Encrypt.
# Wildcard Docker-compose
Download the following docker-compose.yml file and modify it to:
- generate new secrets
- mount your TLS certificates
- mount your
config.yamlconfiguration file
version: "3"
services:
pomerium:
image: pomerium/pomerium:latest
environment:
# Generate new secret keys. e.g. `head -c32 /dev/urandom | base64`
- COOKIE_SECRET=V2JBZk0zWGtsL29UcFUvWjVDWWQ2UHExNXJ0b2VhcDI=
volumes:
# Mount your domain's certificates : https://www.pomerium.io/docs/reference/certificates
- ~/.acme.sh/*.corp.beyondperimeter.com_ecc/fullchain.cer:/pomerium/cert.pem:ro
- ~/.acme.sh/*.corp.beyondperimeter.com_ecc/*.corp.beyondperimeter.com.key:/pomerium/privkey.pem:ro
# Mount your config file : https://www.pomerium.io/docs/reference/reference/
- ../config/config.minimal.yaml:/pomerium/config.yaml:ro
ports:
- 443:443
# https://httpbin.corp.beyondperimeter.com --> Pomerium --> http://httpbin
httpbin:
image: kennethreitz/httpbin:latest
expose:
- 80
# Run
Finally, simply run docker compose.
docker-compose up
Docker will automatically download the required container images for Pomerium and httpbin. Then, Pomerium will run with the configuration details set in the previous steps.
You should now be able access to the routes (e.g. https://httpbin.corp.yourdomain.example) as specified in your policy file.
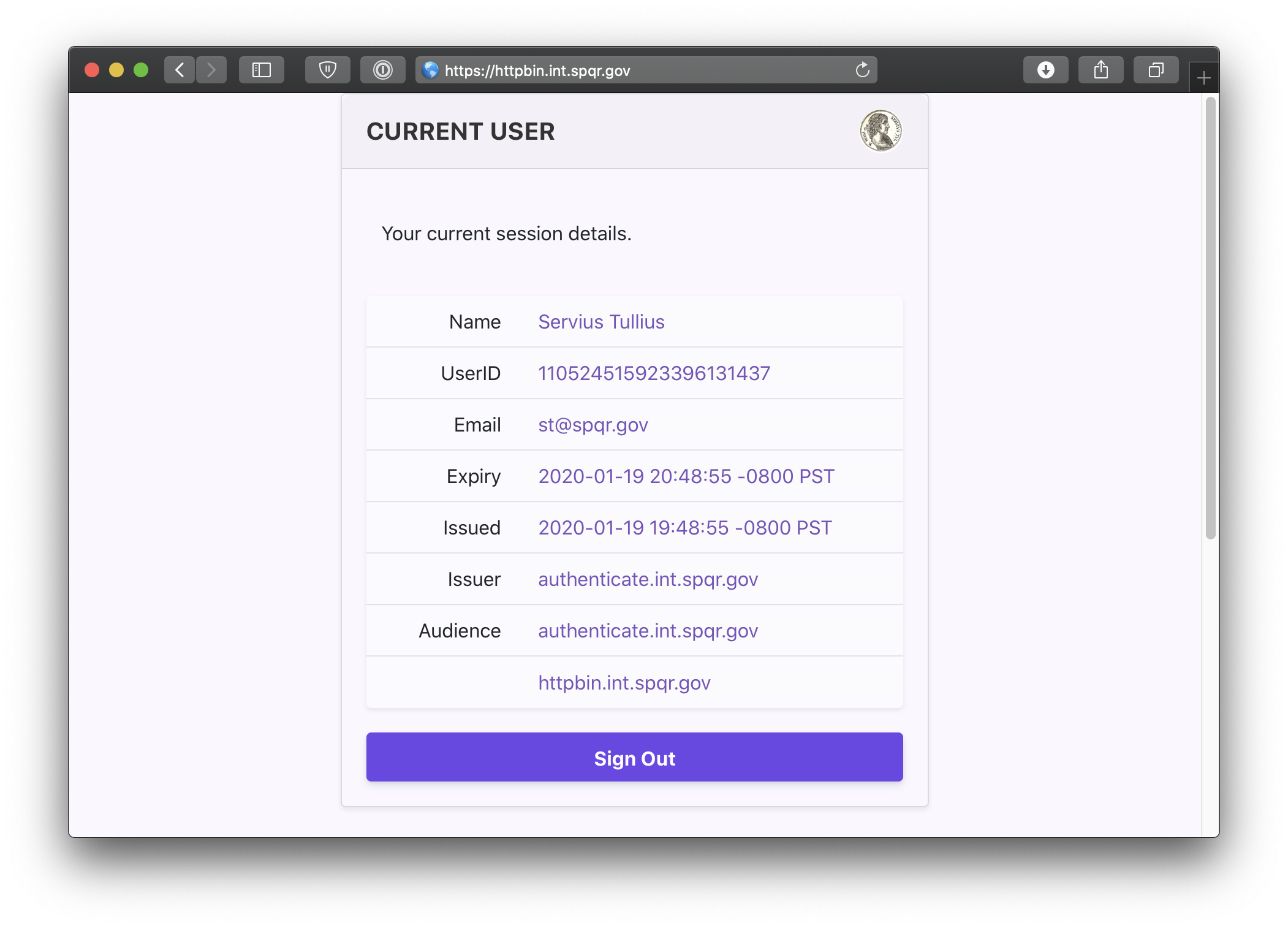
You can also navigate to the special pomerium endpoint httpbin.corp.yourdomain.example/.pomerium/ to see your current user details.